Two years ago, researchers stumbled upon one of the Internet’s most intriguing botnets: a previously undiscovered network of 500 servers, many in well-known universities and businesses around the world, that was impervious to normal takedown methods. After lying low for 16 months, those researchers said, the botnet known as FritzFrog is back with new capabilities and a larger base of infected machines.
SSH servers, beware
FritzFrog targets just about anything with an SSH, or secure shell, server—cloud instances, data center servers, routers, and the like—and installs an unusually advanced payload that was written from scratch. When researchers from security firm Guardicore Labs (now Akamai Labs) reported it in mid-2020, they called it a “next-generation” botnet because of its full suite of capabilities and well-engineered design.It was a decentralized, peer-to-peer architecture that distributed administration among many infected nodes rather than a central server, making it hard to detect or take it down using traditional methods. Some of its advanced traits included:
- In-memory payloads that never touch the disks of infected servers
- At least 20 versions of the software binary since January
- A sole focus on infecting secure shell servers that network administrators use to manage machines
- The ability to backdoor infected servers
- A list of login credential combinations used to suss out weak login passwords that is more “extensive” than those in previously seen botnets
By August 2020, FritzFrog had corralled about 500 machines from well-known organizations into its network. Following the report, the P2P scaled down the number of new infections. Starting last December, Akamai researchers reported on Thursday, the botnet's infection rate increased tenfold and has now mushroomed to more than 1,500 machines.
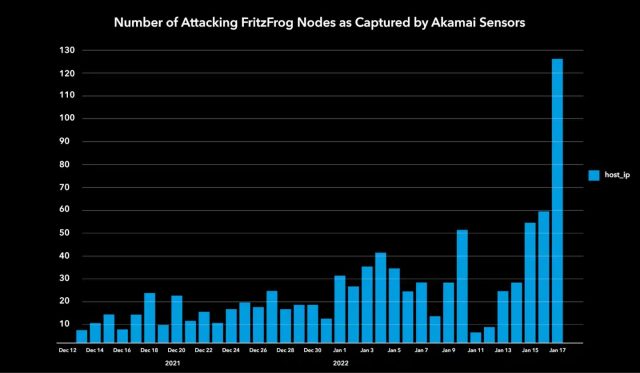
The advanced software is updated daily to fix bugs and over the past several months has implemented new functionality and more aggressive infection methods. Among the organizations it has infected in its latest form are a European television channel network, a Russian manufacturer of health care equipment, multiple universities in East Asia and others in healthcare, higher education, and government.
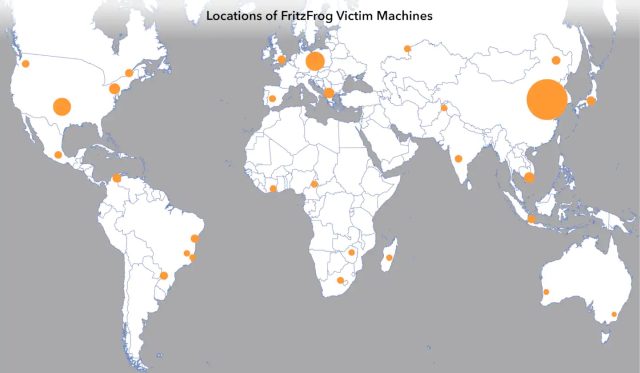
FritzFrog spreads by scanning the Internet for SSH servers, and when it finds one, it attempts to log in using a list of credentials. When successful, the botnet software installs proprietary malware that makes it a drone in a sprawling, headless P2P network. Each server constantly listens for connections on port 1234 while simultaneously scanning thousands of IP addresses over ports 22 and 2222. When it encounters other infected servers, the servers exchange data with each other to ensure all of them are running the latest malware version and have the most up-to-date database of targets and infected machines.
To evade firewalls and endpoint protection software, FritzFrog pipes commands over SSH to a netcat client on the infected machine. Netcat then connects to a “malware server” hosted on an infected machine rather than a central server.
reader comments
69