
Microsoft has again disabled the MSIX ms-appinstaller protocol handler after multiple financially motivated threat groups abused it to infect Windows users with malware.
The attackers exploited the CVE-2021-43890 Windows AppX Installer spoofing vulnerability to circumvent security measures that would otherwise protect Windows users from malware, such as the Defender SmartScreen anti-phishing and anti-malware component and built-in browser alerts cautioning users against executable file downloads.
Microsoft says the threat actors use both malicious advertisements for popular software and Microsoft Teams phishing messages to push signed malicious MSIX application packages.
"Since mid-November 2023, Microsoft Threat Intelligence has observed threat actors, including financially motivated actors like Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674, utilizing the ms-appinstaller URI scheme (App Installer) to distribute malware," the company said.
"The observed threat actor activity abuses the current implementation of the ms-appinstaller protocol handler as an access vector for malware that may lead to ransomware distribution. Multiple cybercriminals are also selling a malware kit as a service that abuses the MSIX file format and ms-app installer protocol handler."
The Sangria Tempest (aka FIN7) financially-motivated hacking group has previously been linked to REvil and Maze ransomware after their involvement in the now-defunct BlackMatter and DarkSide ransomware operations.
In a private Microsoft threat analytics report seen by BleepingComputer, FIN7 was also connected to attacks targeting PaperCut printing servers with Clop ransomware.
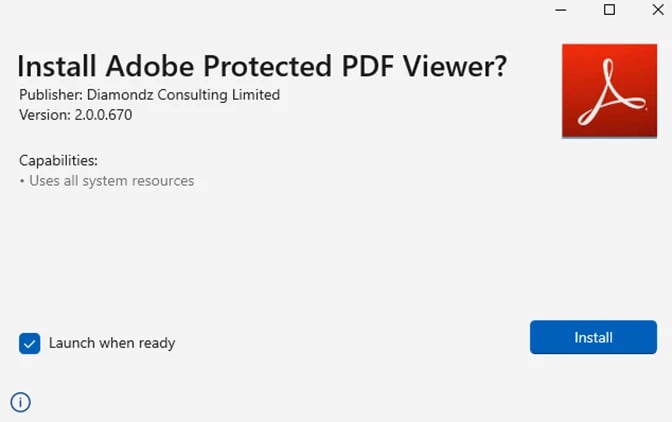
Emotet and BazarLoader malware attacks
As BleepingComputer reported over two years ago, Emotet also used malicious Windows AppX Installer packages camouflaged as Adobe PDF software in December 2021 to infect Windows 10 and Windows 11 systems.
Additionally, the AppX Installer spoofing vulnerability was exploited to distribute the BazarLoader malware using malicious packages hosted on Microsoft Azure, using *.web.core.windows.net URLs.
Microsoft previously disabled the ms-appinstaller protocol handler in February 2022 to thwart Emotet's onslaught.
Since devices compromised as part of these attacks may also be targeted with ransomware, Redmond disabled the ms-appinstaller protocol handler once again earlier this month.
While Microsoft says that it was disabled by default today, December 28, 2023, others report that the change was pushed out earlier this month. However, it is unclear when and why Microsoft reenabled the Windows App Installer between February 2022 and December 2023.
Today, Microsoft recommended installing the patched App Installer version 1.21.3421.0 or later to block exploitation attempts.
The company also advised admins who can't immediately deploy the latest App Installer version to disable the protocol by setting the Group Policy EnableMSAppInstallerProtocol to Disabled.
Top 10 MITRE ATT&CK© Techniques Behind 93% of Attacks
Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.











Comments
NoneRain - 1 year ago
You can mass-update the package running "winget upgrade Microsoft.AppInstaller", but it should be updated automatically from the Microsoft Store.
Right now, it is at 1.21.3482.0.
MS team did a terrible job with their URI installer... everyone saw this coming; they abused it the first time, and now again. Why would you introduce a way to easily install apps while bypassing OS security and "allowing" spoofing, is beyond me.
PTCruiserGT - 1 year ago
And yet, reputable vulnerability detection vendors don't include the disablement of EnableMSAppInstallerProtocol, as insecure as it is, as a finding.