
As India completes two years of the National Mission on Quantum Technologies and Applications (NM-QTA), the time is ripe to reflect upon the implications of quantum technology on cybersecurity. Though quantum computing is in its infancy and commercially available applications are a few years away, India can gain competitive advantage if it leverages on domestic talent, infrastructure, and knowledge.
Quantum computing offers unfathomable opportunities as well as poses potential risks in the cyberspace. One such area of concern is cryptography. Quantum computers can be double-edged swords. On the one hand, quantum-based cryptography protocols, known as quantum key distribution (QKD), will be able to provide secure, airtight communication, on the other hand, quantum computers will also be able to disrupt and hack into existing encryption algorithms, leaving communication insecure, thus, increasing cybercrimes and challenging national security.
With some countries having achieved quantum advantage, the risk of others falling prey to cyber-attacks is going to grow manifold. India has just entered the race to quantum supremacy, and against this backdrop, it needs to examine its quantum roadmap to make it more application-oriented and concentrate efforts on long-term implications of the technology on cyberspace.
Implications of quantum technology on cryptography
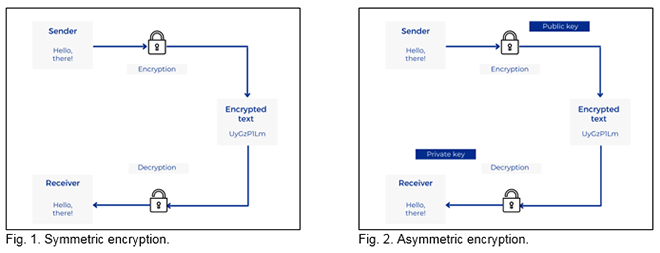
At present, all communication is secured using two major encryption techniques: Symmetric encryption and asymmetric encryption. In symmetric encryption, both the sender and the receiver have identical encryption and decryption keys. If a secure method is used for communication, this type of encryption is relatively safer against quantum-based cyber-attacks.
On the other hand, asymmetric encryption, also known as public-key encryption, uses a pair of keys, one used for encryption and one for decryption. A public key is used for encoding the message and a private key is used for decoding the message. Asymmetric encryption methods like the RSA use algorithms which allow the rightful owner of the private key to decrypt the message. These keys are difficult to hack for a classical computer as data encoded for the receiver’s public key can only be decoded by his private key.
Fig.1 and Fig. 2 show the two kinds of encryption that are used in modern-day communication.
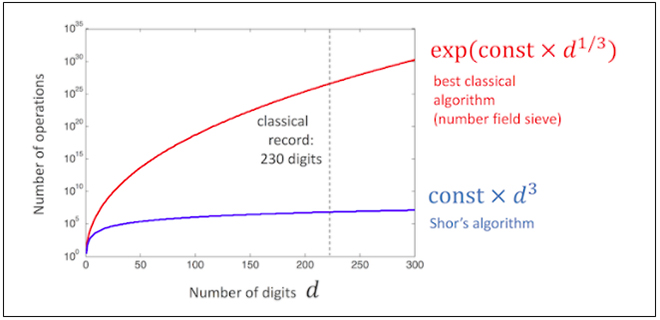
When quantum computers become a reality, these encryption mechanisms will become obsolete. Modern-day public-key cryptography is based on the assumption that conventional computers can manipulate large numbers easily, like multiplying large prime numbers, but cannot find the factors of this large product without years of processing. This means that public-key cryptography is easy to carry out in one direction but cannot be backtracked easily. However, in the 1990s, a Professor of mathematics at MIT, Peter Shor, developed a theory that quantum computers will have the ability to break down large numbers (integers) into their primes in the blink of an eye. This is called the Shor’s algorithm, and it holds immense power over public-key cryptography. Fig. 3. details on the Shor’s algorithm.
Fig. 3. Shor’s algorithm, indicating the power of quantum computers to break large integers into their prime factors.
 Source: IBM.
Source: IBM.
Experts opine that a quantum computer with a compute power of this nature is practically some years away, governments all over the world have started investing heavily into quantum-resistant cryptography. Indian Space Research Organization (ISRO) made a breakthrough in quantum communication in 2021 by developing an entanglement-based satellite communication system, but India must increase capabilities in post-quantum cryptography as well to match pace with China and the United States (US).
Cybersecurity risks and vulnerabilities
When quantum computers and related cryptography become commonplace, they can be manipulated to compromise cybersecurity in many ways.
As has been the case with the uptake of most other technologies, it is highly likely that Indian organisations and businesses will adopt quantum-resistant cryptography in haste. This can put existing systems, infrastructure, and cybersecurity at risk. Thus, the transition to quantum-resistant cryptography should be well-designed and planned in stages.
Also, as end-to-end systems get more deeply connected, there is a need to secure the entirety of cyber ecosystems. Organisations cannot merely protect communication channels and devices to secure sensitive data and information, but will also need to chalk out roadmaps to safeguard critical cyber infrastructure.
Another vulnerability that needs to be acknowledged is the launch of cyberattacks by quantum computers. The current threat detection software is incapable of identifying the signatures and behaviour of such attacks. Hackers can easily masquerade them, making it difficult to identify the first few of such malicious attacks.
Aligning India’s quantum efforts
The risks that quantum computers impose on current cryptography algorithms are significant. Both the government and corporations will be faced with great challenges if public-key cryptography becomes easily compromised by quantum computers. For example, securing digital signatures and identities will become critical. Privacy and data protection will be at risk. This opens gateways for India to secure its cyberspace in two major ways.
Firstly, to avoid the perils of cybercrimes in the quantum age, all three major players in the quantum ecosystem: Government, industry, and academia, must come together to develop quantum-resistant cryptography, also known as post-quantum cryptography. This will, indeed, take years to formalise, develop, and standardise. India should invest in resources for developing on Ramanujan’s graphs for post-quantum cryptography, which can help safeguard critical government and personal information in the quantum era. India can also invest into research and development of homomorphic encryption, which allows organisations to work on encrypted data without decrypting the information. However, building on post-quantum cryptography will not come easy. The foreseeable challenges using more intensive quantum-resistant cryptography will be focused on testing and increased compute time.
India can also invest into research and development of homomorphic encryption, which allows organisations to work on encrypted data without decrypting the information.
Second, quantum-based cryptography, called quantum key distribution (QKD), should also be developed. This paradigm uses concepts of quantum mechanics like entanglement and superposition as the basis of cryptography algorithms. Communication using QKD can be secured using satellite links and optical fibre. QKD will require the use of quantum-based infrastructure, like special hardware, which will significantly increase costs.
Thus, most countries are directing their quantum initiatives towards building quantum-resistant cryptography, except for China, which is also heavily investing in QKD using both fibre and satellite links.
Of the two methods, developing QKD and its requisite infrastructure will be a long-drawn process and will take at least a decade before it can be practically applied. Therefore, governments, academia, and the private sector should invest parallelly in quantum-resistant cryptography to secure communication.
Securing the cyberspace in quantum times
A few key considerations can help secure cyberspace in the quantum age. Like, the present-day public-key encryption infrastructure took several decades to be formalised, standardised, and adopted, and making another such transition to quantum-resistant and/or quantum-based encryption will be challenging. For this, the government should work in cooperation with academia and the private sector to create communication campaigns and help raise awareness about the importance of a timely switch to quantum-enabled encryption. It will also need special infrastructure which should push businesses, startups, and investors in India to plan and invest in systemic development.
Simultaneously, investment and advancement in quantum computing should be made sustainable. With the NM-QTA, the government has allocated a budget of INR 8,000 crores towards research and development of quantum technologies in India for a period of five years (2020–24). The government must also encourage public-private partnerships for translating research into commercial applications and enable the investor ecosystem to support budding quantum startups. At the same time, the research and development roadmap must be periodically reviewed to keep the country abreast of global developments.
The government should work in cooperation with academia and the private sector to create communication campaigns and help raise awareness about the importance of a timely switch to quantum-enabled encryption.
Also, improved collaboration and knowledge sharing within India’s quantum ecosystem needs a significant thrust. The quantum landscape in India is small and in its initial stages with just a few hundred researchers in academia spread across top science and technological institutes of India. Raman Research Institute, one of the pioneers in quantum communication in India, has a dedicated lab working on optical quantum technologies. The Institute of Mathematical Sciences and Harishchandra Research Institute have theoretical working groups while IIT Bombay, IIT Madras, IISc Bangalore, IISER Pune, Tata Institute of Fundamental Research, and IISER Mohali have both experimental and theoretical groups to develop on quantum technologies. With such research and development efforts, it is crucial that a formal knowledge exchange framework be developed at the central level to help all stakeholders keep track of the work done in the field of quantum encryption and open pathways for improved collaboration.
Another key consideration is to have dedicated policy measures in place. While NM-QTA is meant for all things quantum, there is a need to develop a separate policy that addresses cybersecurity in the quantum age. A multi-stakeholder system which includes cybersecurity experts, quantum cryptography researchers, technology policy specialists, and those engaged in maintaining India’s national security (like officials of the Ministry of Defense) should come together to formulate a national-level policy that safeguards data privacy and protects against cybercrimes in the quantum era.
Lastly, timely risk assessment is going to be critical. Risks and vulnerabilities associated with quantum encryption techniques should be mapped well ahead in time and devolve strategies to mitigate them. These should include assessment of datasets that are critical to national security and sensitive personal information, and feasibility of quantum-resistant and QKD algorithms. Since standardisation will be time consuming, relevant agencies should not wait for quantum-related encryption to become a reality, should rather be proactive.
Concluding remarks
The applications of quantum computing will propel governments and businesses to rethink how they secure confidential information and protect the information of the common man. As computing and communication become more complex with the coming of quantum tech, cybersecurity implications should be at the core of all quantum initiatives and the relevant stakeholders should expedite development of post-quantum cryptography.
The views expressed above belong to the author(s). ORF research and analyses now available on Telegram! Click here to access our curated content — blogs, longforms and interviews.






 PREV
PREV


