A new report from Malwarebytes Labs highlights the threats MSSPs have faced since January.

Managed security service providers (MSSPs) have had their hands even more full since the COVID-19 pandemic began. Hackers, already intent on exploiting vulnerabilities, ramped up efforts to take advantage of peoples’ confusion and fear — and the businesses MSSPs protect were no exception, according to Malwarebytes Labs’ new report, “Cybercrime Tactics and Techniques: Attack on Home Base.”
Threats to enterprises grew especially problematic as organizations sent employees home from the office. Cybercriminals went into overdrive. Suddenly, with workers all over the world accessing company resources through VPNs, cloud services and video conferencing, largely over personal devices and home networks, opportunity soared. Bad actors rolled out campaigns designed to trick users into installing malware that stole login data. It also gave attackers remote endpoint control.
Indeed, hacking volume and trickery both reached new heights, according to Malwarebytes Labs. And chances are, MSSPs combated what the cybersecurity firm saw in terms of COVID-19-specific messaging, “from an email purporting to come from UNICEF, to another claiming to contain information about proper face mask usage, to a much-discussed, fraudulent map posing as a legitimate, global coronavirus case tracker from John Hopkins University,” as David Ruiz, Malwarebytes’ content producer, notes in a blog.
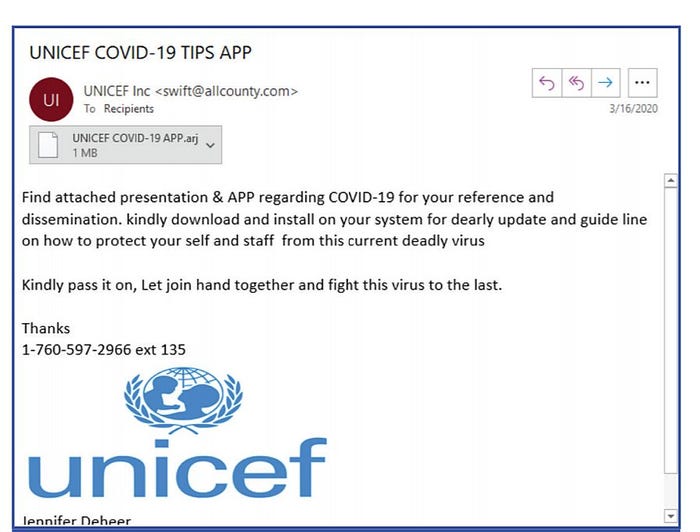 The activity highlights what many MSSPs dealt with between January and March (the period covered in the second-quarter “Cybercrime Tactics and Techniques” report).
The activity highlights what many MSSPs dealt with between January and March (the period covered in the second-quarter “Cybercrime Tactics and Techniques” report).
Breaking It Down
Specifically, Malwarebytes Labs uncovered the following findings:
Cybercriminals quickly transitioned to delivering years-old malware with brand-new campaigns that targeted the confusion, fear and uncertainty surrounding COVID-19.
The backdoor malware NetWiredRC lay low for roughly five months in 2019. But activity dramatically escalated at the start of 2020, with detection up at least 200% by March from December.
January to February was, for several of the malware types analyzed, a precursor to even greater, increased detection activity between February and March.
Malwarebytes recorded increased detections of nearly 110% between February and March for the malware AveMaria. AveMaria is a dangerous remote access trojan that can provide remote desktop access and remote webcam control. It also gives the ability to steal passwords.
Malwarebytes recorded increased detections of more than 160% between February and March for the malware DanaBot. That’s an invasive trojan and information stealer that can swipe online banking account credentials.
Phishing campaigns still appear to be the most popular attack method. But cybercriminals have also gotten creative with fraudulent websites that hide malware.
A 26% increase in credit card skimming activity in March puts home shoppers at greater risk.
Not only do these discoveries show what MSSPs have battled since the beginning of the year, they further point to what cybersecurity professionals stand to face in the coming months as COVID-19 shows no signs of disappearing.
Social Engineering Tests
One important way MSSPs can try to thwart hackers is through continued social engineering tests. Send emails that look legitimate, yet that ostensibly would come from cybercriminals, to educate workers. When an employee clicks through an email and its links, make sure that message leads to an internal company page customized to each client’s logo and needs. The site must contain detailed insight into what constitutes phishing attempts, so workers can better learn what tends to fool them. In addition, provide an email address where employees can send potentially suspicious messages. That way, MSSPs can investigate without lay workers putting devices, connectivity or the organization’s confidential information risk.
Finally, keep enterprises and their staff informed about the different types of threats in circulation, especially those that seek to capitalize on the best of human nature. People want to help others during COVID-19; and, as Malwarebytes Labs explains in “Cybercrime Tactics and Techniques,” hackers want to exploit those good intentions.
“We found a scam email that preyed on individuals’ desire to offer support during the pandemic,” Ruiz said. “We investigated activity from a reported Pakistani state-sponsored threat actor spreading a remote access Trojan through a coronavirus-themed spearphishing campaign. [And] we discovered countless impersonating emails and snake-oil pitches hiding a variety of keyloggers, ransomware and data stealers.”
“Cybercrime Tactics and Techniques: Attack on Home Base” goes in-depth about the varieties of threats Malwarebytes Labs identified, including the AveMaria Remote Access Trojan; the backdoor NetWiredRC malware; the LokiBot botnet; the AZORult malware; DanaBot banking trojan malware; card skimmers; and state-sponsored attacks.
Read more about:
MSPsAbout the Author(s)
You May Also Like


