A huge number of websites around the world are endangered by an unpatched vulnerability in the PHP scripting language that attackers are already trying to exploit to remotely take control of underlying servers, security researchers warned.
The code-execution attacks threaten PHP websites only when they run in CGI, or common gateway interface, mode, Darian Anthony Patrick, a Web application security consultant with Criticode, told Ars. Sites running PHP in FastCGI mode aren't affected. Nobody knows exactly how many websites are at risk, because sites also must meet several other criteria to be vulnerable, including not having a firewall that blocks certain ports. Nonetheless, sites running CGI-configured PHP on the Apache webserver are by default vulnerable to attacks that make it easy for hackers to run code that plants backdoors or downloads files containing sensitive user data.
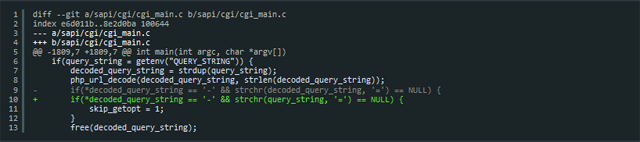
Making matters worse, full details of the bug became public last week, giving attackers everything they need to locate and exploit vulnerable websites.
"The huge issue is the remote code execution and that's really easy to figure out how to do," Patrick said. "If I as an attacker found it existed on a particular site, it would be exciting because I own everything. It's the kind of vulnerability where it's probably not super prevalent, but if it's there, it's not a minor thing."
According to security researcher Ryan Barnett, exploits are already being attempted against servers that are part of a honeypot set up by Trustwave's Spider Labs to detect Web-based attacks. While some of the Web requests observed appear to be simple probes designed to see if sites are vulnerable, others contain remote file inclusion parameters that attempt to execute code of the attacker's choosing on vulnerable servers.
"Because this is honeypot stuff and we're not actually running all of these live applications, we can't be sure what I'm showing actually would work," Barnett told Ars. "We just wanted to show that yes, bad guys are actively scanning for this."
In a series of Twitter dispatches made in response to this article, blogger Trevor Pott said he's seeing a dozen such attack attempts every hour against smaller websites including his own, trevorpott.com. They appear to be made by infected computers located in the US and China for the purpose of seeding them with malware used in drive-by download attacks.
What's more, the open-source Metasploit framework used by hackers and penetration testers to exploit known vulnerabilities has been updated to include the exploit, providing a point-and-click interface for remotely carrying out the code execution attacks. Making matters worse, an update PHP maintainers released late last week to patch the hole can easily be bypassed, leaving vulnerable websites at risk even after applying the fix.
Patrick said websites that run PHP in CGI mode should install the update anyway and then follow several steps to mitigate their exposure, including applying a second patch published last week by researchers on Eindbazen.net. Barnett's post also includes steps webmasters can follow to protect themselves against exploits.
HD Moore, the CSO of Rapid7 and the Metasploit chief architect who wrote the PHP-CGI module, agreed with Patrick that the percentage of sites vulnerable to the bug is probably small. But he went on to say the installed base of PHP is so big and the damage to those who are susceptible to attack is so large that admins should take immediate steps to lock down their systems right away. He also said it's likely that attacks could last for months or years because of the difficulty many administrators have in updating.
"I wouldn't be surprised if we continue to see this bug exploited in the wild for two or three years because it will take a while for people to patch their systems," he told Ars. "There are a lot crusty old boxes out there running old versions of PHP, and if those are configured as CGI it's going to affect it."
Story updated to make clear PHP running in FastCGI mode isn't vulnerable and to provide details provided by blogger Trevor Pott.
reader comments
27