In the world of computer systems used to flip switches, open valves, and control other equipment inside giant electrical substations and railroad communications systems, you'd think the networking gear would be locked down tightly to prevent tampering by vandals. But for customers of Ontario, Canada-based RuggedCom, there's a good chance those Internet-connected devices have backdoors that make unauthorized access a point-and-click exercise.
That's because equipment running RuggedCom's Rugged Operating System has an undocumented account that can't be modified and a password that's trivial to crack. What's more, researchers say, for years the company hasn't bothered to warn the power utilities, military facilities, and municipal traffic departments using the industrial-strength gear that the account can give attackers the means to sabotage operations that affect the safety of huge populations of people.
"You treat these embedded appliances as a device that you don't have a window to see into," says researcher K. Reid Wightman of industrial machinery, which is often designed to withstand extreme heat and cold, dust, and other brutal conditions where they're housed. "You can't really patch it. You have to rely on the vendor to do the right thing when they set the device up and when they install the OS. And the vendor really fell down on this one."
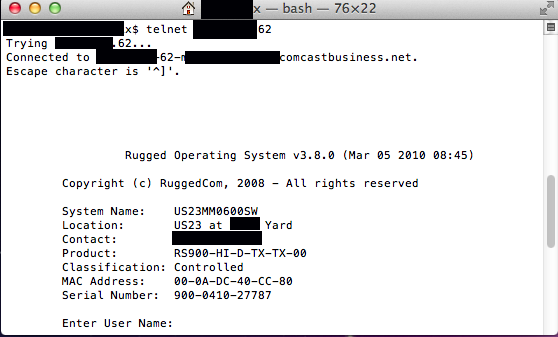
The backdoor uses the login ID of "factory" and a password that's recovered by plugging the MAC, or media access control, address of the targeted device into a simple Perl script, according to this post published on Monday to the Full Disclosure security list. To make unauthorized access easy, paying customers of the Shodan computer search engine can find the IP numbers of more than 60 networks that use the vulnerable equipment. The first thing users who telnet into them see, as the picture above demonstrates, is its MAC address.
Like a router plugged into a utility's power grid
Equipment running the Rugged Operating System act as the switches and hubs that connect programmable logic controllers to the computer networks used to send them commands. They may sit between the computer of a electric utility employee and the compact disk-sized controller that breaks a circuit when the employee clicks a button on her screen. To give the equipment added power, Rugged Operating System is fluent in the Modbus and DNP3 communications protocols used to natively administer industrial control and SCADA, or supervisory control and data acquisition, systems. The US Navy, the Wisconsin Department of Transportation, and Chevron are just three of the customers who rely on the gear, according to this page on RuggedCom's website.
"As a citizen and based on the customer list on their website, I know for a fact that I personally depend on this equipment every day in some way," said Justin W. Clarke, the author of the full-disclosure advisory who said he notified company officials of the backdoor 12 months ago. "The equipment is so widely installed that it would be logical to assume that something I'm doing—whether it's riding a train, using power, or walking across a cross walk—depends on this."
RuggedCom representatives didn't respond to a request for comment. This article will be updated if a response is received after its initial publication.
According to a timeline included in Clarke's advisory, RuggedCom officials earlier this month stated "they need another three weeks to alert their customers, but not fix the vulnerability." Working with the US Computer Emergency Response Team, Clarke said he sought additional information, but RuggedCom never responded.
Forever day bugs bite again
In acknowledging but not fixing a security vulnerability in software that's widely used to control critical infrastructure, RuggedCom joins a growing roster of companies marketing wares bitten by so-called forever-day bugs. The term, which is a play on the phrase zero-day vulnerability, refer to documented flaws in industrial systems that will never be fixed. Other members of this group include ABB, Schneider Electric, and Siemens. Indeed, RuggedCom was acquired by a Canada-based subsidiary of Siemens in March.
The hardcoded backdoor can be opened when users access affected devices using telnet, remote shell, or a serial console. The best defense against attacks that exploit the vulnerability is a layered approach that includes isolating devices from the Internet altogether as well as disabling or blocking telnet and remote shell access through network filters or firewalls, Clarke said.
An independent security researcher in San Francisco, Clarke told Ars he has grown so concerned about the lack of security in industrial control systems that he's taken to ordering used gear hawked on eBay to see what kinds of vulnerabilities he can find in it. He said he spotted the Rugged OS backdoor with little trouble by analyzing an image of the RuggedCom firmware.
"It is esoteric, it is obscure, but this equipment is everywhere," he said. "I was walking down the street and they had one of the traffic control cabinets that controls stop lights open and there was a RuggedCom switch, so while you and I may not see it, this is what's used in electric substations, in train control systems, in power plants and in the military. That's why I personally care about it so much."
This article was updated to remove identifying information included in the image.
Listing image by Photograph by s0.geograph.org.uk
reader comments
50